Desktop Authenticator
Problem Statement
I was unlocking my phone 15 times a day just to copy 2FA codes. Authy has a desktop app, sure, but it syncs your secrets to their cloud — and once you work in identity security, that starts to feel uncomfortable. I wanted something that stays on my machine and doesn't phone home. So I built it.
Hypothesis
There's a gap between "phone authenticator" and "enterprise SSO." Desktop power users who care about privacy have basically no good options. Also — if you have to look at a 2FA app dozens of times a day, it might as well not look boring.
Solution
Desktop Authenticator is a macOS Electron app that generates TOTP codes locally with encrypted storage and zero external data transmission:
- TOTP generation — standard RFC 6238 time-based codes, auto-refreshing every 30 seconds with a visual countdown
- Multiple QR input methods — file upload, drag-and-drop, clipboard paste (⌘V), and screenshot capture for maximum flexibility
- Encrypted local storage — secrets stored in a SQLite database with
electron-storeencryption. Nothing leaves the device - Minecraft-themed UI — pixelated VT323 font, block-style elements, dark mode support. Makes the mundane act of copying codes feel intentional
- Native macOS integration — menu bar presence, keyboard shortcuts, system dark mode detection
Screenshots
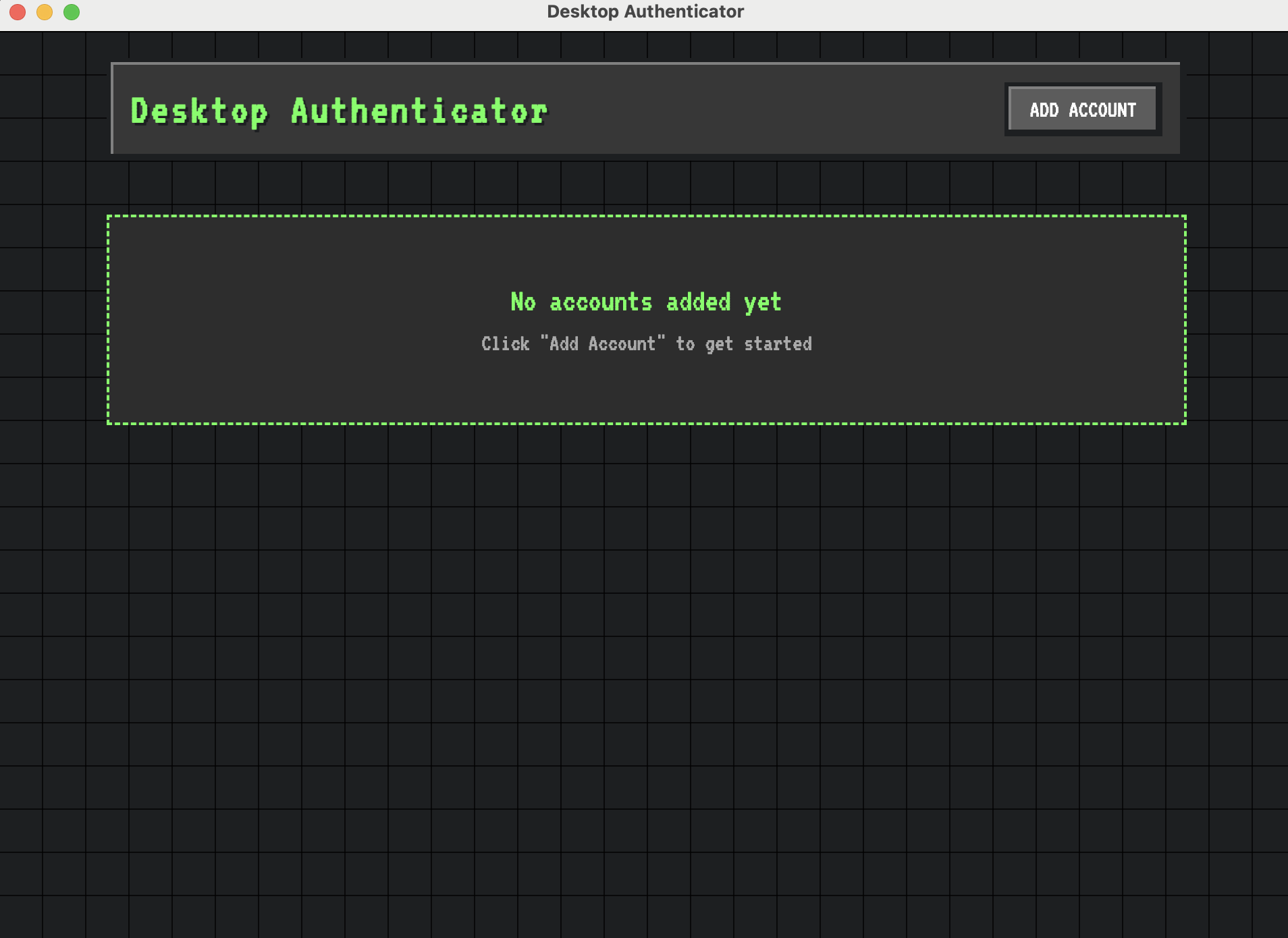
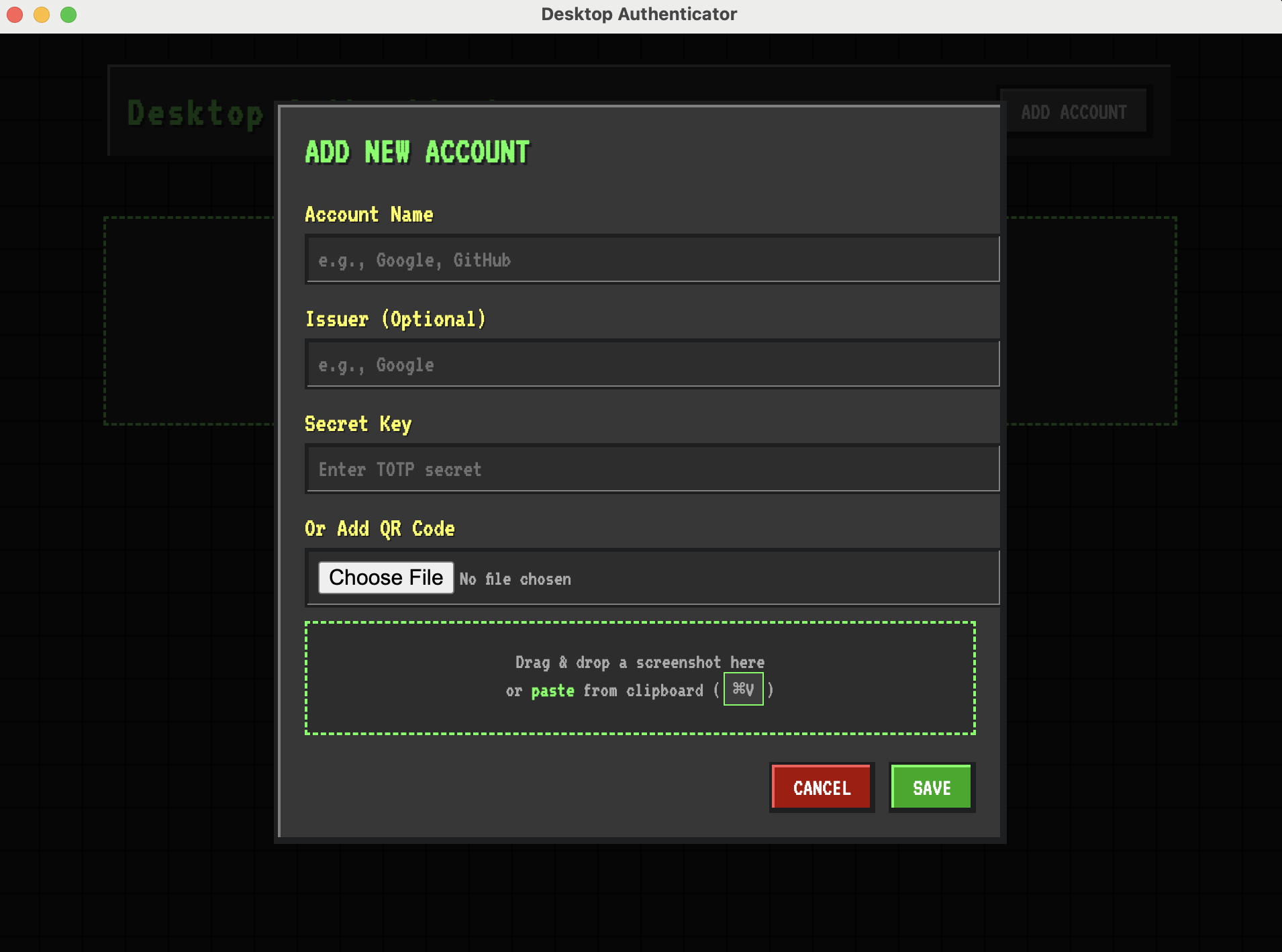
Technical Architecture
Fully air-gappable. No network calls, no telemetry, no cloud sync. Packaged as .dmg and .zip.
Key Product Decisions
- Desktop-first, not mobile — deliberately chose the underserved surface. Mobile authenticators are abundant; desktop ones that respect privacy are rare
- Local-only by design — no sync feature, no account system. This isn't a limitation — it's the core value proposition. Users who want cloud sync already have Authy
- Minecraft theme as differentiation — authenticator apps are commoditized. The theme creates emotional attachment to a utility tool — users remember and reach for it because it's theirs
- Multiple QR input paths — onboarding friction kills 2FA adoption. Supporting 4 input methods (file, drag, paste, screenshot) means users can always get their secrets into the app regardless of source format
Impact & Metrics
Lessons Learned
- Security products succeed on trust, not features. The single most important "feature" is what the app doesn't do — it doesn't phone home, doesn't sync, doesn't require an account. Absence of risk is the product
- Personality in utility software creates loyalty. The Minecraft theme sounds frivolous but it turns a forgettable tool into something users actively choose over alternatives. Delight matters even in security tools
- Electron gets a bad rap, but for this use case it's ideal. The app needs to process images, read QR codes, and manage a database — all things Electron handles well. It doesn't need to be a 5MB native Swift app; it needs to work reliably